
Fortinet FortiOS Software
Network Security Operating System

Overview:
The World’s Most Advanced Security Operating System
FortiOS is a security-hardened, purpose-built operating system that is the foundation of all FortiGate® platforms. FortiOS 5 software leverages the hardware acceleration provided by custom FortiASIC™ processors, delivering the most comprehensive suite of IPv6-ready security and networking services available within a single device.
Complete Security
Fortinet designed and built FortiOS 5 to deliver the advanced protection and performance that standalone products simply cannot match. The services work together as a system to provide better visibility and mitigation of the latest network and application threats, stopping attacks before damage can occur.
Unmatched Performance
FortiOS 5 enables high performance, ultra low latency multi-threat security by leveraging the hardware acceleration provided by purpose-built FortiASIC processors. This combination of custom hardware and software gives you the best security and performance possible from a single device.
Unique Visibility and Control
Advanced security features such as Flow-based Inspection and Integrated Wireless Controller capability allow you to monitor and protect your network from endpoints to core, and from remote offices to headquarters, for wired and wireless traffic. FortiOS allows greater traffic visibility and more consistent, granular control over users, applications and sensitive data.
Increased Simplicity
FortiOS 5 lowers costs and reduces IT staff workloads. Physical or virtual FortiGate appliances give you the flexibility to match your security to your environment while enforcing a uniform security policy. Single pane of glass management and centralized analysis ensure consistent policy creation and enforcement while minimizing deployment and configuration challenges.
More Security, More Control, More Intelligence
Building on our history of innovation, FortiOS 5 includes over 150 new features and enhancements to help you fight advanced threats, securely integrate mobile devices and build smart policies.
More Security - Fighting Advanced Threats
|
|
More Control - Securing Mobile DevicesYou can secure you mobile device and BYOD environments (including iOS®, Android® and Windows® clients) by identifying devices and applying specific access policies as well as security profiles, according to the device type or device group, location, and usage. |
|
More Intelligence - Building Smart Policies For Smart SecurityFortiOS 5 gives you intelligent, automatic adjustment of role-based policies for users and guests based on location, data, and application profile. Enhanced reporting and analysis provides deeper insights into the behavior of your network, users, devices, applications and threats. |
Key FortiOS Features:
With over 40 new features, Fortinet engineers have enhanced virtually every aspect of the operating system, including the addition of two distinct services, Data Leakage Prevention and WAN Optimization, which have previously been available as standalone products only. Other features extend existing services, such as an identity-based policy feature, which allows the FortiGate’s firewall policies to be defined by user or group. Multiple enhancements to the existing intrusion prevention service allow passive IDS support, and also make the intrusion prevention service IPv6 ready.
|
|
Fighting Advanced Threats:
Cybercriminals today are organized, sophisticated and have powerful resources at their fingertips. In most cases, attacks are initiated with specific targets and objectives in mind. The aim is to infiltrate hosts in networks and steal valuable data. The data may be personal information, accounts or intellectual property. This information can be used for future attacks (second stage) to further penetrate networks.
These attacks are often crafted to evade common traditional security tools, such as firewalls, intrusion prevention systems and antivirus gateways. This is referred to as advanced evasion techniques, or AETs. They're low-profile, targeted and stealthy, avoiding notice and suspicion. These threats are a combination of malware – executable code running on the attack target – and exploits for vulnerabilities, weaknesses on a system. These exploits can attack what is known as a zero-day vulnerability, a software flaw to which there is no patch, update or fix. These attacks usually cannot be detected by signature-based filters that compare them to known attacks. Other advanced threats include spearphishing, impersonation and polymorphic malware.
Threats that we see today typically adopt a six-stage lifecycle:
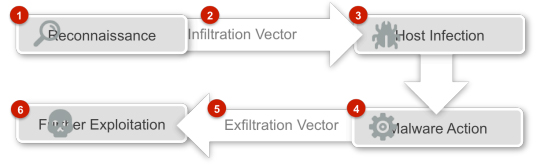
- Reconnaissance
Unlike typical malware infiltration, advanced threats either perform initial probes towards targets or collect information about them by various means, such as phishing, social engineering or obtaining intel from other infected hosts. - Infiltration Vector
Armed with relevant information, these threats infiltrate their targets in various ways – these are also known as attack vectors. Think of these vectors as things like phishing emails, malicious flash (SWF) or PDF documents, malicious websites that attack flaws in browsers like Internet Explorer or Firefox. Phishing emails can be targeted and very convincing, with the goal to get the victim to click on a malicious link or open an attachment. These are known as spear phishes. - Host Infection
To evade traditional security systems, malware transmissions are typically encrypted and arrive via unexpected routes like corporate email with a file share invitation or a prompt for software updates from an impersonated site. There are many tricks that modern malware employ, including security software evasion – code specifically designed to destroy antivirus processes running on the system. Another trick is polymorphism, code that shifts shape constantly to escape signature-based antivirus detection. - Malware Action
Once the malware is installed, it often attempts to initiate a call back, using common transmission methods that are allowed by typical security policies. Otherwise, it keeps a low profile, generating no activities that are likely to be noticed. It remains in sleep mode, awaiting further instructions. Increasingly, malware is aware of its environment and won't allow itself to be detected in a virtual machine sandbox. - Exfiltration Vector
The exfiltration usually involves the surreptitious delivery of stolen data via often encrypted but common channels, such as HTTPS, back to the command center or to another compromised system controlled by cybercriminals. - Further Exploitation
With successful communication links between the command center and the compromised hosts, further exploitation is easy to accomplish. These malicious acts include attempts to access materials the host has connection to, such as documents on servers, cloud-based applications and database credentials.
Best Practices against new advanced Threats: Advanced Persistent Defence
In order to defend against advanced threats, organizations must update and adjust existing network security and adopt new security implementations.
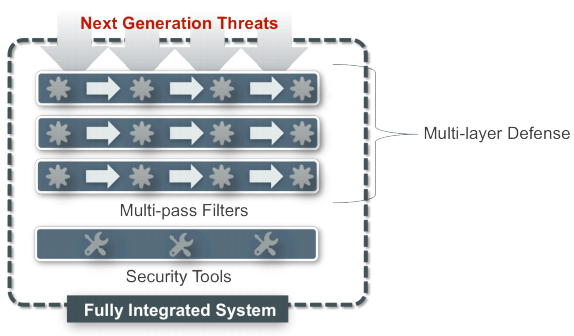
The challenge is to add protection to the network without straining budgets, resources or performance. The components of a comprehensive approach are:
- Multi-layer Defense System
- Multi-pass Anti-Malware Protection
- Integrated Systems & Security Tools
Multi-layer Defense System
Next generation threats use multiple vectors of attack to exploit weak defenses, avoid detection and increase the odds of penetration.
To detect these threats, organizations can no longer simply rely on a single solution; multiple layers of defense are needed to fill possible network security gaps. Multi layer defense seeks to detect polymorphic malware, prevent receipt of phishing emails, block connection to compromised websites, and deny malware access to its command channel.
Multi-pass Anti-Malware Protection
Detecting and blocking stealthy malware is becoming more challenging. Many malicious codes are now designed to evade traditional signature-based filters. Although antivirus signatures remain a critical part of the solution, new proactive real-time technologies that don't rely on signatures are necessary for air-tight protection. An intelligent virus inspection engine is key to proactively detect these threat
Cloud-based services with real-time databases and robust processing resources are also an important component.
Integrated Systems & Security Tools
Cybercriminals no longer work alone. They use coordinated expertise and share resources, producing disparate components that challenge many typical network security implementations. It's difficult to collate information to identify and deter these advanced threats.
It's important to integrate security components in the network, including threat and network activity correlations. Deploying an integrated security platform can yield even more benefits, like efficient traffic processing, with better network performance and low-latency communications.
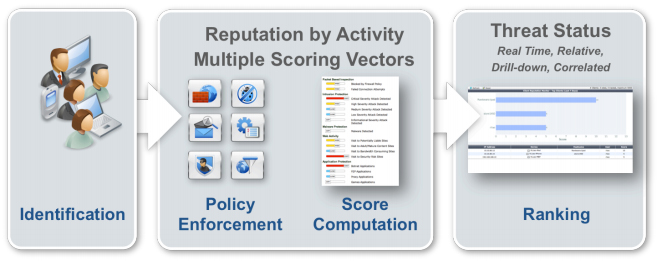
There should be abilities to correlate threat landscape information, enabling administrators to use a cumulative security ranking of network terminals to spot suspicious activities that might evade detection in a typical isolated setup. This client reputation capability allows administrators to detect signs of advanced threats within their networks and set up appropriate responses. Most malicious infections are the result of exploits on vulnerable hosts, particularly those with out-of-date operating systems and application patches, weak passwords or poorly configured security settings. Vulnerability scans are one of the most useful tools against these threats, identifying weaknesses before the bad guys do.
How FortiOS 5 fights next generation threats
FortiOS 5 has enhanced anti-malware capabilities, including file analysis with intelligent sandboxing and a botnet IP blacklist. We introduced the patent-pending client reputation system to assist administrators in protecting their networks with advanced analytics and controls.
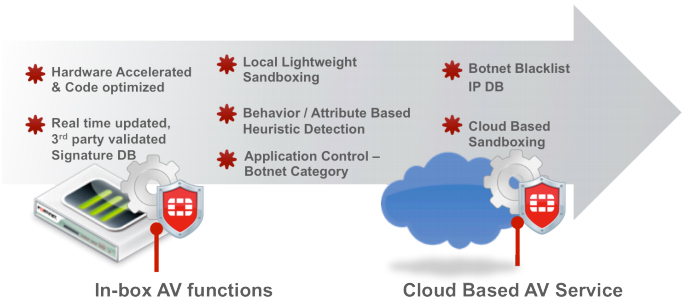
FortiOS 5 includes:
- AV Signatures
Detect and block known malware and most of its variants. Highly accurate with few false positives. The signature approach is backed by a sophisticated antivirus engine that can detect polymorphic malware. In fact, the signatures are quite intelligent. For example, one single signature can detect over 50,000 polymorphic viruses in some scenarios. - Behavioral and attribute-based heuristic detection
Detects and blocks malware based on a scoring system of known malicious behaviors or characteristics. This detects malware that doesn't match a signature, but behaves similarly to known malware. Used to flag suspicious files for further analysis, either local or cloud based. - File Analysis
Detects new threats by running suspicious files in a contained emulator to determine whether they're malicious. This technique is resource-intensive and may impact performance and latency while increasing visibility for zero-day or previously unknown threats. Modern malware is written to detect such analysis machines, however Fortinet's file analysis engine has lots of technology built in to defeat these countermeasures cyber criminals employ. - Application Control
Detects and blocks known botnet activities by examining traffic that passes through the gateway. Also effective in preventing zombies from leaking data or communicating instructions. This is known as chatter. By identifying and blocking chatter, these threats are mitigated since it doesn't matter what URL, domain, or IP the infected host is trying to connect to. - Botnet Servers Backlist Filter
Detects and blocks known botnet command and control communication by matching against blacklisted IP addresses. Stops dial-back by infected zombies.
FortiGate AV Engine 2.0
The new engine is designed to detect and block today's advanced threats. It provides inline file processing capability that utilizes the FortiGate's hardware acceleration component.
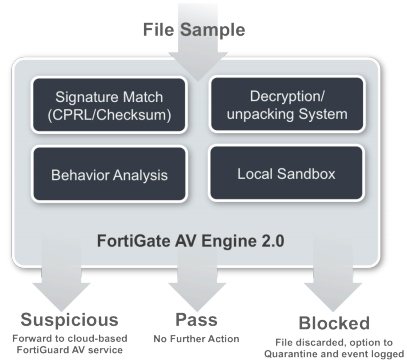
- Signature Match Processor
The signature match processor uses the unique and patent-pending Compact Pattern Recognition Language (CPRL), which is optimized for performance without compromising accuracy. With CPRL, a single signature is able to cover well over 50,000 different viruses, including zero-day virus variants as previously mentioned. The processor also performs blacklisted file checksum matching for common large-volume static malwares. To achieve this, FortiGuard analysts go through intensive training to write optimized CPRL signatures. - Decryption/Unpacking System
Most modern malware is compressed or encrypted to evade traditional file matching systems. This system unveils the actual content for further analysis to detect stealthy polymorphic malware. Think of it as matching the inner components, or true DNA of a virus. - Local Sandbox
This system consists of various OS-independent emulators and uses intelligent filetyping to execute suspicious codes, such as malware that uses JavaScript obfuscation. - Behavior Analysis Engine
This heuristic engine performs behavioral and attribute-based analysis to detect zero-day malicious code for further analysis. It looks at the intent of a virus – what is it trying to do based on the executable code that is analyzed by the engine.
New FortiGuard Services
The new FortiGuard services are cloud-based capabilities that enhance the detection and provide real-time protection against next-generation threats.
Unlike some competitors' solutions, file submissions to FortiGuard services are minimal since the in-box local engine captures most malware.
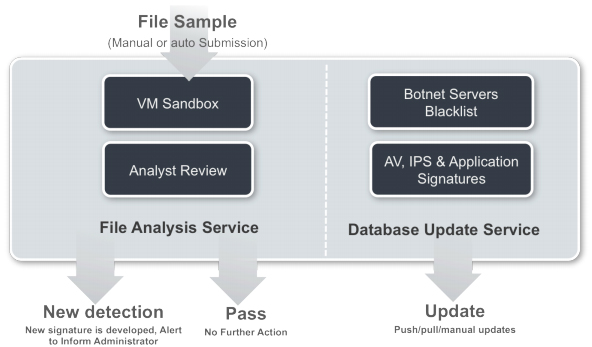
- Cloud Based Sandbox Environment & File Analysis
The sandbox environment consists of various operating system simulators that execute suspicious programs and compute a Bayesian score based on lists of activities and attributes. FortiGuard antivirus researchers are based around the world, providing 24x7 round-the-clock malware analysis. New viruses and variants are examined to provide accurate detection, reduce false positives and discover new evasion techniques. When these techniques are discovered, researchers work side by side with Fortinet development to built in the appropriate technology to defeat evasion techniques. - Database Updates
Up-to-date signatures are essential in stopping malicious activities in the network. Apart from regular antivirus, intrusion prevention systems and application control signatures, FortiOS 5 introduces a new botnet blacklist database. With this new database, users will be able to prevent zombies in the network from communicating to botnet servers.
Conclusion
With FortiOS 5, Fortinet has taken the fight against advanced threats to a new level, breaking the lifecycle of today's malware to ensure comprehensive security without compromising performance.
Securing Mobile Devices:
Organizations are increasingly dependent on mobile information technology in every activity. Employees rely heavily on more and more portable network devices that allow them critical flexibility to roam for increased productivity. But mobile devices put networks at increased risk of data leaks and exposure to malicious infection.
The BYOD phenomenon
BYOD (bring your own device) started out as an informal trend that saw staff using smartphones and tablets in the workplace to access privileged internal resources. These devices rely heavily on network connectivity for many of their functions and applications.
However, it quickly evolved to include a broader phenomenon of the use of a variety of devices in the workplace that aren't controlled by the corporation that hosts them.
Employees like bringing their own devices for the familiarity, ease of use and, by extension, access to the organization's applications. Companies embrace BYOD because it allows employees increased mobility, higher job satisfaction and greater efficiency and productivity.
Although BYOD brings new advantages to the workforce, it also brings its fair share of challenges. Many of these challenges revolve around security. The most significant problem for IT departments is the lack of visibility and control of these devices.
Unmanaged devices
These are typically wifi devices brought in by employees. Users access the network, logging in on their smartphones, tablets or laptops with their usual credentials, but the devices can evade security policies because they're not a formal part of the enterprise's managed environment. Yet installing a host agent to manage these devices can be unwelcome and intrusive to the owner of the device.
And, unlike corporate equipment, personal mobile devices often run on different operating systems (and many different versions of operating systems), making the installation of a host agent difficult, if not impossible.
Personal devices can also add to network misuse, with applications such as internet radio and video streaming
Corporate mobile devices
These are portable devices issued by the corporation, so they're more likely components of the managed network environment than purely personal devices. But when they're out of the corporate network, they're out of the range of the security policy enforced by the security gateway.
In both cases, mobile devices can be lost or stolen. Without proper control, they can also be used to leak corporate data, inadvertently or maliciously.
How FortiOS 5 secures mobile devices
There are three elements to the FortiOS 5 solution for securing mobile devices; identification, access control and security application.
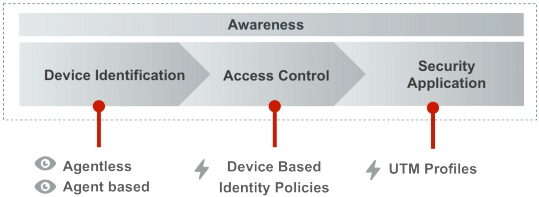
Device identification
FortiOS 5 identifies all devices, wired and wireless, and their operating systems in two ways:
- Agentless detection
Agentless detection identifies devices that log on to the network without requiring additional software on the devices themselves. It utilizes a broad range of measures to accurately determine device type, with traditional TCP and MAC vendor code fingerprinting, the use of DHCP attributes, and application layer analysis including HTTP user agent and SIP message parsing. These measures can be updated via our FortiGuard network as the device landscape evolves. - Agent-based identification
For agent-based identification, FortiClient is installed on devices to feed information directly to FortiOS. This technique is the most reliable and allows identification even when the devices are on remote networks.
Access control
After devices are identified, they're automatically assigned to device groups according to type and OS. Administrators also have the ability to create custom groups for policy enforcement.
Security Application
The administrator can then control access and assign security profiles based on device groups or individual devices. These profiles include web content filtering and application control.
For example, a school can set policies where teachers can access server resources, while students only access permitted areas of the Internet, avoiding plagiarism sites and other inappropriate content. In addition, to prevent bandwidth abuse, students are blocked from streaming multimedia. Or a corporation that uses contractors on its guest network can allow their devices access to project-specific resources while allowing only internet access to other guests.
Device contextual information for visibility
Device identification also allows the FortiGate to provide new contextual information in status widgets and logs. This allows administrators to better understand their network posture and identify problem spots quickly.
Endpoint control with off-net protection
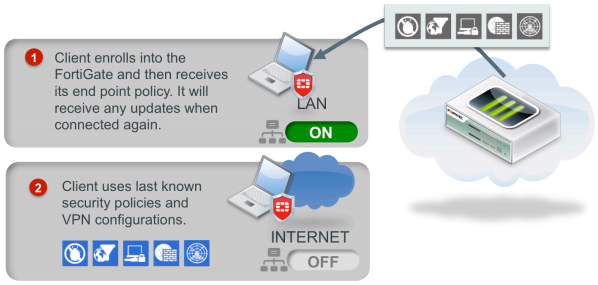
When mobile devices leave the local network and go "off-net", they're no longer protected by a security gateway. The tight integration between FortiClient and FortiOS provides off-net protection, reducing corporate vulnerability to malware infection and data leaks and enforcing corporate access policies. Adopting endpoint control allows users not only to bring their own devices, but to take their security policy home.
Web filtering, for example, can block malicious and phishing sites even when the user is telecommuting or web browsing. The user can access the Internet safely anywhere without needing a VPN. When a VPN is required to connect to corporate resources, FortiOS distributes new VPN configurations to roaming devices.
Synchronizing fixed and mobile security policies allows the simple implementation of updates and modifications to ensure up-to-date protection.
Conclusion
The combination of FortiClient and FortiOS 5 provides a powerful solution ensuring the most appropriate level of security is present on all devices, at all times, in all places.
Making Smart Policies:
Today, the network is everywhere, and with it, the expectation of continuous connectivity. But to maintain security, organizations demand more visibility and control. Control of what applications are accessed, from where, when and by whom. Traditionally, IT departments have tried to solve this complex problem with more complexity.
Taming the complexity of security policies
Administrators have typically created policies with precise granularity to yield more secure networks. But policy accumulation and complexity is a problem. As a security gateway sits in the network for years, rules are constantly added but seldom removed. The risk increases as the "holes" get bigger; complexity increases and control decreases. Security is breached.
Administrators find it increasingly hard to understand the security that's actually being implemented by this bloated set of security policies. A complex system is a fragile one.
An oversized policy list also makes troubleshooting difficult. Administrators have to spend more time examining how traffic is affected by the rule set. Unfortunately, this also results in even more unnecessary ad-hoc or "hot patch" rules, further decreasing security.
How FortiOS 5 can help set up smart policies
FortiOS 5 makes policy creation easier and more efficient.
Policy Consolidation
Traditionally, network access policies are configured separately from other security policies, very often on separate systems.
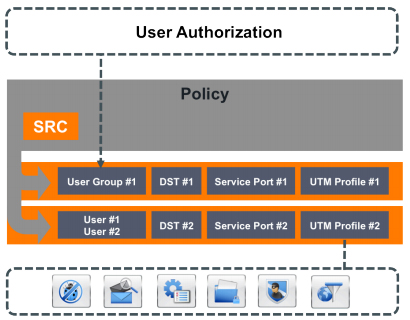
FortiOS 5 implements comprehensive user authorization technologies so administrators can configure access policies along with security policies. Network access can be configured for wireless and wired networks, supporting a variety of entry modes such as captive portals and 802.1x.
The ID-based policies of FortiOS 5 provides an authorization model which, after successful authentication, determines where you can go, what applications you can use and what information you can access.
The system seamlessly determines which destinations, services, applications and profiles are applied. Depending on the ingress interface a user logs into (for example, a wireless LAN in the lobby or on the wired desktop), different policies can be intelligently assigned.
Reusing user credentials with a single sign-on
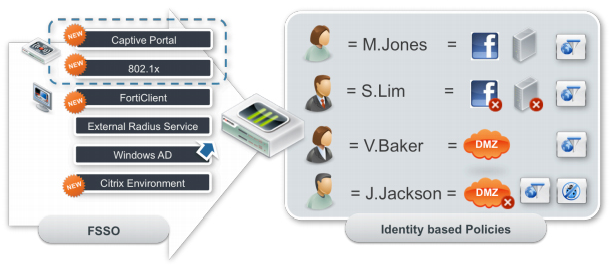
FortiOS 5 FSSO (Fortinet Single Sign-On) framework provides a single sign-on from a diverse range of authentication environments, allowing you to use and reuse credentials. This includes:
- Windows AD
- External radius authentication
- Citrix/terminal service
- Network access via 802.1x, WEP, captive portal, etc.
- FortiClient single sign-on
Complex implementations simplified
Traditionally, some security implementations require complex setup and configuration. FortiOS 5 simplifies them.
- Guest Access
Temporary secured network access for guests is essential. FortiOS 5 makes it easy by providing:- Integrated guest administration portal for personnel such as a receptionist who provides guest access.
- Random credential generation so that every guest can be uniquely identified.
- Time quota to ensure guest access expires appropriately, preventing unnecessary exposure.
- Dynamic Remote VPN
Client VPN provisioning and setup has been a constant challenge to administrators. FortiOS 5 makes setup easier and more secure by reducing the potential for misconfiguration. With tight FortiClient integration, SSL and IPSEC client configurations can be provisioned and updated easily. FortiClient also now includes enterprise VPN capabilities such as auto redundant VPN gateway selection.
Providing deep knowledge for administrators
FortiOS 5 provides detailed visibility, critical in helping administrators quickly understand network and system status, configurations and threats.
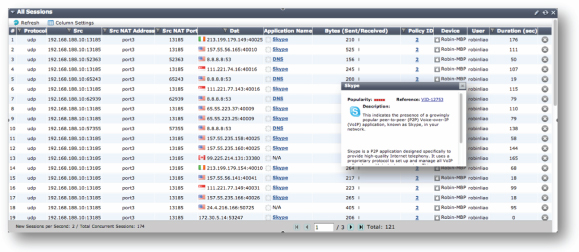
Comprehensive contextual and unified information is now available on status widgets, logs and reports. This includes information such as:
- Device identity, operating system and hostname
- Identity of user and user groups
- Pop-up information from our FortiGuard Threat Encyclopedia
- Applications, their category and risk type
Conclusion
Smart policies break the spiral of increasing complexity by unifying access and security policies, providing a powerful and accurate tool for the security administrator.
Specifications:
FortiGate—Purpose-Built Hardware, Software, and Services
FortiGate platforms are based on an integrated hardware, software, and services architecture specifically designed for improved security and performance in perimeter, core, and data center environments. The FortiASIC™ Content Processor (CP) is a key component in FortiGate security platforms; providing a hardware scanning engine, hardware encryption, and real-time content analysis processing capabilities. The FortiASIC Network Processor (NP) series of processors provides acceleration for firewall, encryption/decryption, signature and heuristic packet scanning, and bandwidth shaping. FortiOS security applications can be selectively enabled to provide a full suite or a unique set security services all within a single platform. The FortiGuard™ network dynamically updates system software and security services such as antivirus, antispam, Web filtering, antispyware, and intrusion prevention to ensure the maximum level of protection is being provided.
| FortiOS Security Services: | ||
|---|---|---|
System Administration:
Visibility:
FortiGuard Services:
Routing & Network Services:
High Availability:
User Based Identity:
OTP Token Server:
|
Device Based Identity:
Endpoint Control:
Client Reputation:
User Notification:
Firewall:
VPN:
IPS:
Application Control:
Antivirus:
Email Filter:
Web Filter:
|
DLP:
Vulnerability Scanning:
Wireless Controller:
SSL Offloading & Inspection:
WAN Optimization:
Virtual Systems:
Log & Report:
IPv6:
Others:
|
Note: This list may not be complete. Features may not be available to all FortiGate models. Please refer to FortiOS 5.0 release notes and administration guide.
Documentation:
Download the Fortinet FortiOS Software Datasheet (PDF).
